Services: Information Security
ISO 27001:2022 (ISO27001) is an International Standard that has been prepared to provide a model for establishing, implementing, operating, monitoring, reviewing, maintaining and improving an Information Security Management System (ISMS).
ISO 27001 provides an ISMS a framework for implementing these principles using the ‘Plan - Do - Check - Act cycle and management system processes. The implementation of ISO27001 is an ideal response to legal and contractual requirements and potential security threats such as:
- Misuse
- Hacking
- Penetration
- Theft
- Viral attack
Risk assessment – Organisations conduct an Information Security Risk Assessment.
Security design and implementation – Organisations incorporate security as an essential element of information systems and networks.
Security management – Organisations adopt a comprehensive approach to security management.
Awareness - Organisations are aware of the need for security of information systems and networks, plus what they can do to enhance security.
Responsibility - Organisations are responsible for the security of information systems and networks.
Response – Organisations act in a timely and co-operative manner to prevent, detect and respond to security incidents.
How the organisation can benefit from ISO27001:2022:
- It can act as the extension of other Management Systems (ISO9001, ISO14001 and ISO45001) to include security.
- It provides an opportunity to identify and manage risks to key information and systems assets.
- Provides confidence and assurance to trading partners and clients; acts as a marketing tool.
- Customer satisfaction by giving confidence that their personal information is protected, and confidentiality upheld.
- Business continuity through management of risk, legal compliance and vigilance of future security issues and concerns
- Legal compliance by understanding how statutory and regulatory requirements impact the organization and its customers.
- Improved risk management through a systematic framework for ensuring customer records, financial information and intellectual property are protected from loss, theft and damage.
- Proven business credentials through independent verification against recognised standards.
- Ability to win more business particularly where procurement specifications require.
- Allows an independent review and assurance to you on information security practices.
The information security management system services provided by QSP Solutions include:
- Implementation and operation of information security management system to ISO27001:2022.
- Information security policy statement, information security objectives and procedures [a copy of the MS04 Information Security Policy is available by clicking here]
- Identifying compliance with information security and other regulations.
- Development of information security management programmes.
- Delivery to staff of employee ISO27001 and information security awareness training sessions [an ISO27001:2022 Awareness Briefing is available by clicking here]
- Undertake and manage information security internal audit programme, including audits, audit reports and support through to resolution of any issues arising.
- Liaison with the chosen certification body for certification to ISO27001:2022.
- Maintenance of the ISO27001:2022 management system post certification.
An ISO27001:2022 Action Plan is available by clicking here [clicking here]
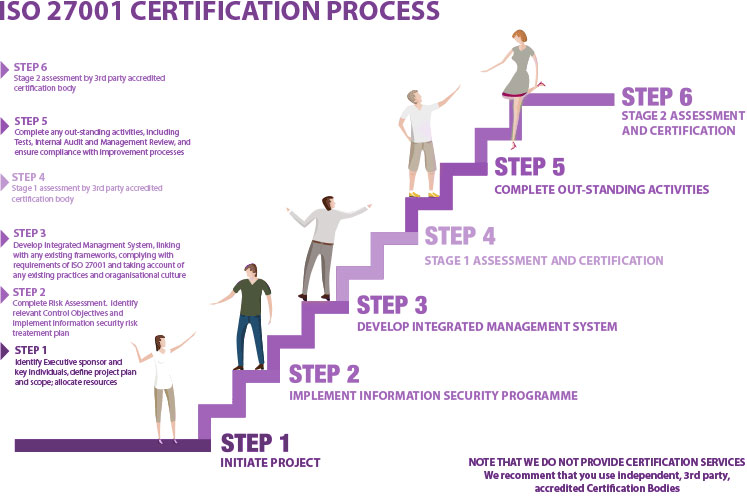
The clauses of ISO27001:2022 are:

- Scope
- Normative references
- Terms and definitions
- Context of the organization
- Leadership
- Planning
- Support
- Operation
- Performance evaluation
- Improvement
An ISO27001:2022 Clauses is available by clicking here [clicking here]

 Services
Services

